If you’re website is hosted on our platform or not, this blog post is for you. A new feature that will allow automatic updating of plugins and themes will be available in WordPress version 5.5, which is scheduled to be released on August 11, 2020. This update also comes with security updates and more but we’re going to touch on some of the main points.
What Happens During an Automatic Update?
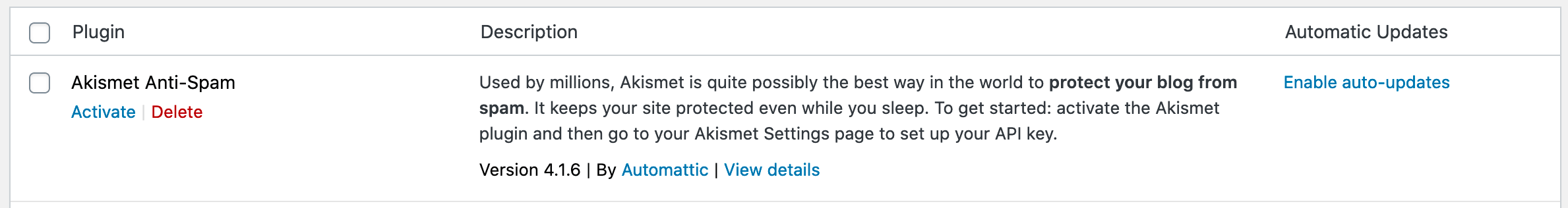
Auto-updates for plugins and themes will be turned off by default upon release, meaning that auto-updates will not be automatically enabled when WordPress 5.5 is rolled out. Site owners will have to visit the theme or plugin dashboard to enable auto-updates and choose which packages to automatically update when a new version of the plugin or theme is available. Site owners can choose to turn on auto-updates for all of the installed plugins, choose to auto-update some of their plugins, or choose not to turn on auto-updates for any plugins whatsoever.
These automatic updates are what operations engineers refer to as “unattended updates,” meaning that the code of plugins and themes are updated and deployed without the site owner’s participation. They may get triggered while a site owner is on the site publishing, they may get triggered overnight when a site owner is asleep, or during the day when the site owner is in the middle of an important meeting. The site owner will receive an email that updates have taken place, but if they miss that email, they might not know until they log in again and see a new version of the updated plugin or theme.
This marks a major shift from the attended updates currently required in WordPress. Currently, each plugin and theme update requires that the site owner or administrator initiate the updating process to download and install a new version of a plugin or theme.
In rare cases, some plugins have auto-updates built in and are already updating automatically. Wordfence is one of these plugins. Wordfence has offered an optional auto-update feature for several years to help keep our customers secure.
Why is WordPress Core Adding Automatic Updates?
One of the most prolific vectors of WordPress malware infections is the presence of vulnerabilities in out-of-date plugins, themes, and less frequently, WordPress core. By adding automated updating features to WordPress plugins and themes in the WordPress 5.5 core release, the core team looks to improve the security of WordPress installations across the board and make maintenance easier for site owners. Rather than having to log in to your WordPress site regularly to perform required plugin and theme updates, your site will run “unattended” updates when updates to installed plugins and themes are made available within the WordPress repository.
Problems and Pitfalls of Automated Updating
Unattended auto-updating of any code base is not without possible problems, and WordPress themes and plugins are not unique in this respect. Even attended updates can present difficulties. When the health and safety of your site is at stake, making an informed decision is critical. As such, we developed a few scenarios where auto-updates could cause potential problems such as site outages, data corruption, malicious content, among other undesirable effects.
Not all of these scenarios may affect you and your WordPress site. Below are a few caveats to keep in mind when determining what risk level your organization faces by enabling auto-updates.
- Concurrent auto-updates can fail. If a number of plugins have updates within a few hours, and wp-cron triggers them all to auto-update concurrently, this could lead to auto-updates failing on a server where resources are over utilized. If a triggered auto-update fails for any reason, the site may experience fatal error messages. In rare cases, plugins might become deactivated, or a site could be taken offline or stuck in maintenance mode.
- Issues may be introduced that limit site functionality without the site owner’s knowledge. For example, let’s say you have a WooCommerce store, and your WooCommerce supportive plugins auto-update while you’re on vacation. One of those supportive plugins has just been auto-updated, and that auto-update makes product checkout on your site impossible. It’s August. You usually have a seasonal slowdown when many people are on vacation, so the drop in sales is not unexpected. Meanwhile, your ecommerce site is essentially not functioning properly and your vacation is interrupted when a customer writes to you days later.
- Difficulty determining “what changed.” Whenever a problem occurs in IT operations, the first question to ask when trying to troubleshoot the problem is “What changed?” If you have two or more unattended updates that have occurred, multiple things have changed and it can become much harder to isolate the root cause of the problem.
- Vulnerabilities can be introduced with new features. With a recent update to the wpDiscuz plugin, new features introduced new vulnerabilities affecting over 80,000 WordPress sites. If your organization does a code review on any new plugin code being deployed to your production WordPress site, auto-updating removes your opportunity to do this code review and potentially catch vulnerabilities before they are deployed.
- Major version releases could have compatibility problems. Occasionally a vendor will put out a major release that makes significant changes to the code, or the database, or both. These higher risk releases could introduce problems, as we have seen with plugins that have a large installation base like Yoast and Jetpack. In April 2020, popular SEO plugin Yoast SEO released a major version release that refactored how information was stored in the WordPress database. This major update caused some sites to have issues that required immediate patching. For major plugin releases, it may make sense to take a “wait and see” approach to ensure the release is stable before deploying. Auto-updates remove your ability to take this approach.
- QA resources vary among plugins. Some plugins have large teams of developers and software quality assurance (SQA or QA) engineers behind them. Other plugins have smaller teams or are powered by a single developer who may be a hobbyist. Enabling auto-updates for plugins with larger teams is lower risk, because the plugin’s own QA team has provided comprehensive test coverage and significantly reduced the risk of anything going wrong with the release. Plugins with individual developers that lack QA resources should be considered higher risk due to the lack of test coverage or lack of testing altogether.
- Lack of canary releasing to test for issues. Canary updates roll out code to a small percentage of sites to check for problems. Chrome/Chromium uses this model to protect the larger install base from catastrophic issues. If no issues are detected, the update then rolls out to the rest of sites. WordPress has not built this system into auto-updates in version 5.5, and thus the auto-updates for a plugin roll out at the same time to the entire user population. This does not provide an early warning system that will reveal a catastrophic problem with a plugin. If you run a mission critical website, you can emulate the canary release process by waiting a few days before updating, for non security related releases. This may be a reason to disable auto-updates, depending on your specific needs.
Auto-updates Sounds Like It Has Problems. Does It Really?
With all of these pitfalls, there are obvious questions about whether or not having auto-updates enabled is a good solution. The biggest question you might have is: why Wordfence and other security experts recommend keeping plugins updated if rapid updating could introduce so many issues?
At the moment, nearly every update you perform on your site is done as an attended update. This means that you initiate the update, you know when your site has updated, you can read the developer’s changelog to determine whether or not it is a critical security update, a bug fix update, or a major release update on which you might want to wait. You can also test your site after every plugin update, and you are more likely to to determine the source of any problems introduced by a problematic plugin update.
Enable this with caution, if you have any questions, please feel free to contact us


Leave A Comment